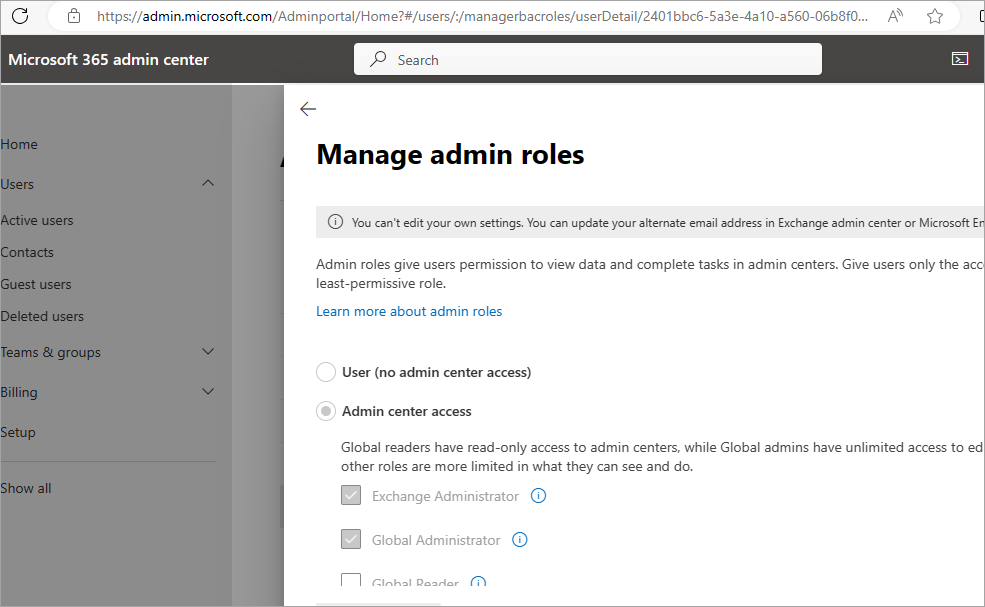
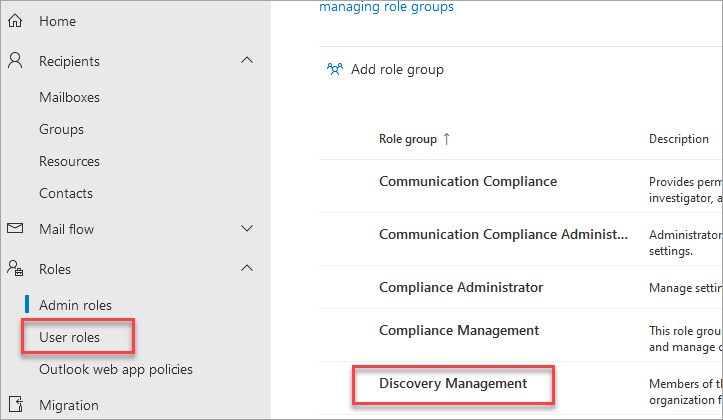
Error
We experienced this error when creating a new Microsoft 365 backup set to back up all M365 accounts in an organisation.
Failed to list sFolderID=null; sPath=Office 365/Users/; Reason=[ExchangeOnlineManager.a] Failed to list path: Office. Error: com.ahsay.afc.cloud.office365.m: does not have enough permission to impersonate user accounts.
Please visit Exchange admin center and add user into “Discovery Management” role group. Also make sure the role “ApplicationImpersonation” has been granted to “Discovery Management”
Cause
When backing up more than one M365 account (email, SharePoint or OneDrive), the permissions must be edited within M365 to allow access to the other accounts. This is a natural security measure to prevent an admin from reading other user’s emails.
We have also seen this error when the permissions are correctly set. If this happens, elevate another user to a global admin and set the permissions below.
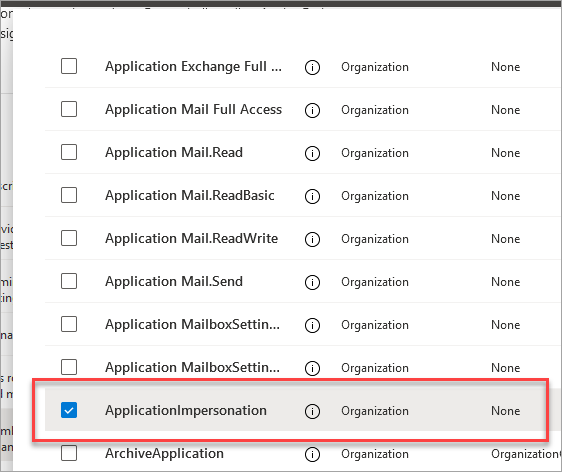
Fix
- Access the M365 Exchange admin center (microsoft.com)
- Click on Roles
- Click on the Discovery Management role
- Assign your account which must be a global administrator to the role
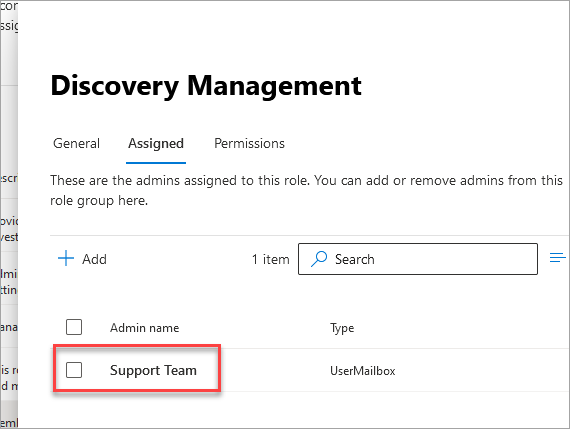
- Add the ApplicationImpersonation permission to the role. This will also add the Legal Hold and Mailbox Search permissions.
The new permissions will be verified once you reauthenticate the M365 account. Because this error only happens before a successful backup can run, it is simpler to recreate the backup set.
Known Errors
[BackupResourceManager.takeSlot] Fail to get subCmd to run, caused by [h] [ExchangeOnlineManager.CloudCache.listDirectFromCloud] Failed to list sFolderID=null; sPath=Office 365/Users/; Reason=[ExchangeOnlineManager.a] Failed to list path: Office 365/Users/. Error: com.ahsay.afc.cloud.office365.m: does not have enough permission to impersonate user accounts. Please visit Exchange admin center and add user into “Discovery Management” role group. Also make sure the role “ApplicationImpersonation” has been granted to “Discovery Management”.